1. Executive Summary
The Department of Veterans Affairs’ (VA) mission is to serve America’s Veterans and their families with dignity and compassion, to be their principal advocate, and to ensure that they receive the medical care, benefits, social support, and lasting memorials for which they are eligible because of their service to our Nation. As part of its mission, VA shares a vast amount of Veteran and VA mission-critical privacy information. This includes sensitive personal information (SPI) and protected health information (PHI) (collectively referred to as “personally identifiable information” or “PII”) across the organization and with VA partners. Protecting this data, complying with applicable privacy laws, and managing privacy risk is extremely important to maintain VA’s standing as a trusted organization.
This Privacy Program Plan (PPP) supplements VA Directive 6502, VA Enterprise Privacy Program to formally document the VA Privacy Program. It describes how VA implements Office of Management and Budget (OMB) Circular A-130, Managing Information as a Strategic Resource.
The purpose of the PPP is to provide an overview of the VA Privacy Program. This plan highlights:
- The structure and mission of the VA Privacy Program.
- Resources dedicated to the VA Privacy Program.
- Role of the Senior Agency Official for Privacy (SAOP).
- Strategic goals and objectives of the Privacy Program.
- Program Management controls in place to meet applicable Federal privacy requirements and manage privacy risks.
- An overview of the VA Privacy Program requirements.
This Plan serves as a high-level summary of the VA Privacy Program. The PPP is a living management document designed to accommodate changes in privacy laws, technology, requirements, and standards. VA Administrations (Veterans Health Administration (VHA), Veterans Benefits Administration (VBA) and National Cemetery Administration (NCA)) are encouraged to use it as the foundation for their own PPP when addressing Administration-specific privacy matters.
2. VA Privacy Program Strategic Goals and Objectives
Protecting privacy is fundamental to the successful accomplishment of the VA mission and to maintain the trust Veterans have in VA. The VA Privacy Program has a vision to serve as a model for privacy excellence across the federal government, providing a trusted environment that protects the privacy of Veterans, their beneficiaries and VA employees.
The VA Privacy Program supports the four strategic goals as articulated in the Department of Veterans Affairs Fiscal Years 2022-28 Strategic Plan. It also supports the important cross-cutting goal to build and strengthen Veterans trust in VA by preserving privacy, oversight, and transparency in the execution of all VA activities.
To accomplish the strategic outcomes, there are four VA Privacy Program goals, each supported by specific and measurable objectives:
Goal 1: Ensure VA Maintains Compliance with Federal Privacy Laws, Regulations and Policy
VA commits to achieve excellence in privacy compliance while reducing privacy risks to Veterans, their families, and caregivers. VA develops and implements policies, procedures, and controls to comply with federal privacy laws and regulations. VA regularly reviews and updates its practices to align with evolving federal and VA guidelines, fostering a culture of accountability and integrity in handling PII.
Objective 1.1 – Increase accountability and transparency by enhancing and automating VA’s privacy compliance processes in adherence to the Privacy Act of 1974, E-Government Act of 2002, OMB requirements, and best practices. The privacy compliance process includes the Privacy Threshold Analysis (PTA), Privacy Impact Assessment (PIA) and System of Records Notices (SORNs).
Objective 1.2 – Partner with and provide sound and consistent guidance to VA Administrations and Staff Offices concerning the implementation of Federal privacy laws, regulations, and other best practices, supported by legal advice from the Office of General Counsel.
Objective 1.3 – Report privacy-related complaints and incidents systematically, process efficiently, and mitigate appropriately, according to legal requirements and VA policies and procedures.
Objective 1.4 – Implement a cycle of continuous assessment and improvement to embed and enforce privacy protections. Adhere to privacy requirements and transparency in all VA activities that have a privacy impact.
Goal 2: Deliver Enterprise-wide Privacy Risk
VA is dedicated to managing privacy risks to effectively protect PII and help achieve VA’s mission. VA establishes and uses a multi-level risk management approach that addresses security and privacy risk at the organization, mission, business process, and information system levels. VA executes the Risk Management Framework (RMF) to manage privacy risks that may result from unauthorized access or disclosure of PII; the processing of PII; inadequate quality or integrity of PII; and the lack of appropriate notice, transparency, or participation. VA considers privacy as a part of the ongoing Assessment and Authorization (A&A) of information systems and that privacy risks are at an acceptable level prior to granting an Authorization to Operate (ATO) decision.
Objective 2.1 – Integrate privacy requirements and controls into the enterprise architecture, system development lifecycle, acquisition processes and system engineering processes.
Objective 2.2 – Mature privacy continuous monitoring capabilities to ensure the effective implementation and monitoring of controls to maintain situational awareness of VA’s privacy posture.
Objective 2.3 – Integrate privacy into all governance. Consider privacy as a part of the upfront assessments of Enterprise-wide policy, budget, and programmatic decision making as well as business operations, system development, and related activities.
Objective 2.4 – Establish a systematic, risk-driven process that operationalizes the “Privacy by Design” framework within VA information system development and engineering approaches.
Goal 3: Cultivate a Privacy Risk-Aware Culture
VA ensures that all personnel have a baseline understanding of federal privacy requirements by providing training for new employees and annually thereafter. These programs reinforce the privacy policy implementation and reduce the risk of privacy incidents to our Veterans, their beneficiaries, and VA employees. VA also develops and provides targeted, role-based, specialized training to employees.
Objective 3.1 – Consistently apply privacy requirements across VA workforce to ensure the protection of Veterans, their beneficiaries, and VA employee’s PII.
Objective 3.2 – Develop and deliver advanced and targeted role-based privacy training to employees, including managers, senior executives, and contractors, with assigned privacy roles and responsibilities.
Objective 3.3 – Educate the VA workforce about privacy laws, regulations, and VA policies, fostering a culture of privacy awareness within all activities.
Goal 4: Become the Best Privacy Workforce in Government
VA develops and sustains a highly skilled, diverse, and engaged privacy workforce to accomplish the privacy mission. VA ensures supervisors understand the key role they play in the recruitment, hiring, and retention efforts for privacy positions. VA leverages training and professional development opportunities to develop and manage a high-performing privacy workforce. VA provides privacy leaders and managers with the insight and tools to effectively carry out performance management, organizational learning, and succession planning.
Objective 4.1 – Enhance privacy skillsets to enable a workforce capable of managing privacy risks.
Objective 4.2 – Develop workforce planning and succession strategies to ensure continuity of operations. Strategically situate the VA Privacy Program to successfully meet the growing challenges of the federal privacy community.
Objective 4.3 – Ensure hiring managers take advantage of flexible hiring authorities for privacy positions.
Objective 4.4 – Promote a culture of continuous learning and professional development in support of the privacy mission. Support a comprehensive Privacy Officer training approach that accelerates development and helps Privacy Officers perform better in their jobs.
3. Structure of the VA Privacy Program
The Office of Information and Technology (OIT) manages VA’s Privacy Program centrally. VA distributes Privacy Program roles and responsibilities across VA Administrations, including the VHA, VBA, NCA, and VA Staff Offices. Figure 1 illustrates the VA Privacy Program Organization.
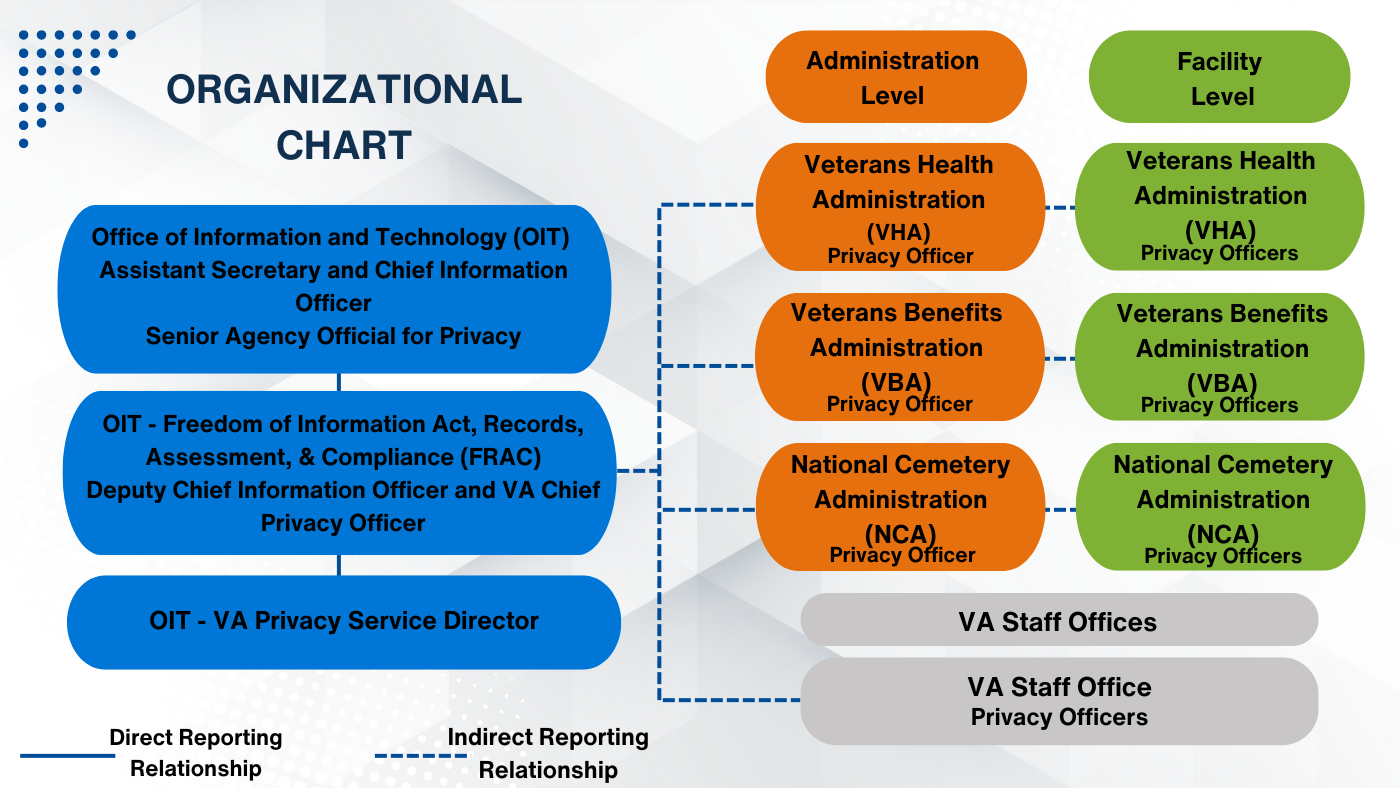
VA Privacy Program Organization Chart
VA Privacy Program has dedicated personnel resources, including VA SAOP, VA Chief Privacy Officer (CPO), VA Privacy Service Director, Administration Privacy Officers, and VA Staff Office and Facility Privacy Officers.
3.1 Senior Agency Official for Privacy
The VA Secretary designated the Assistant Secretary for Information and Technology (ASIT) and Chief Information Officer (CIO) as the VA SAOP to protect privacy interests and responsibly manage PII across the agency. The SAOP is responsible for overseeing, coordinating, and facilitating VA’s compliance with privacy policies, as mandated by Federal legislation, the Office of Management and Budget (OMB), and as described in VA Directive 6502, Enterprise Privacy Program. The SAOP has overall responsibility and accountability to integrate t privacy protections into all VA programs, technologies, policies, and procedures.
The responsibilities of the SAOP include:
- Establishing the VA Privacy Program and providing oversight for the protection of PII.
- Designating a senior executive as VA CPO.
- Serving as the “Agency Steward” for the VA Privacy Program, embodying responsibility for the compliance, enforcement, accountability, and managing the protection of PII.
- Providing guidance and oversight of the VA Privacy Program budget and advocating for privacy solutions throughout the planning, programming, budget, and execution process.
- Ensuring adherence to the Privacy Act and Title 38 United States Code confidentiality statutes in all operations and policies of the VA Privacy Program.
- Serving as the VA member of the Federal Privacy Council as listed in Executive Order 13719, Establishment of the Federal Privacy Council.
3.2 VA Chief Privacy Officer
The SAOP designated the Deputy Chief Information Officer for Freedom of Information Act, Records, Assessment, & Compliance as the VA CPO. The CPO has primary responsibility for implementation and sustainment of VA’s privacy program and related functions delegated by the SAOP.
The responsibilities of the CPO include:
- Administering VA Privacy Program on behalf of the VA SAOP.
- Ensuring Under Secretaries, Assistant Secretaries and Other Key Officials comply with privacy laws and requirements and manage privacy risks within their realm of responsibility.
- Implementing privacy protections commensurate with the risk and magnitude of the potential harm to individuals in all VA operations.
- Integrating privacy and information management processes within Enterprise-level strategic and operational planning and daily business processes.
- Ensuring compliance with information system policies and procedures outlined in VA Handbook 6500, Risk Management Framework for VA Information Systems VA Information Security Program.
- Developing and maintaining mandatory agency wide privacy awareness and training programs according to applicable privacy laws and policies.
- Maintaining a central policy making role in developing and evaluating VA legislative, regulatory, and other policy proposals involving privacy issues.
- Advising on the process for receiving, documenting, tracking, and investigating privacy complaints, incidents, and data breaches.
- Implementing the VA privacy continuous monitoring strategy to maintain ongoing awareness of threats and vulnerabilities that may pose privacy risks. Monitor changes to information systems that create, collect, use, process, store, maintain, disseminate, disclose, or dispose of PII. Conduct privacy control assessments to verify the continued effectiveness of all privacy controls selected and implemented to comply with applicable privacy requirements and manage privacy risks.
3.3 VA Privacy Service Director
The VA Privacy Service Director reports directly to the VA Chief Privacy Officer. The VA Privacy Service Director performs the day-to-day oversight and management of the VA Privacy Program under the supervision of the SAOP and CPO.
The responsibilities of the VA Privacy Service Director include:
- Serving as the key policy advisor on implementing federal privacy requirements to include the Privacy Act of 1974, privacy provisions of the E-Government Act of 2002, OMB Circular A-130, OMB Circular A-108, and other laws, regulations, and policies.
- Overseeing, directing, and establishing the long and short-term goals of the VA Privacy Program.
- Advise and recommend the privacy implications of VA’s planning, programming, and budgeting processes to senior officials.
- Developing policies, procedures, programs, and materials at an enterprise-wide level.
- Managing VA compliance and risk management programs to include PIAs, SORNs and computer matching agreements (CMAs).
3.4 Administration Privacy Officers
VA Administrations (VHA, VBA, and NCA) implement and manage the VA Privacy Program through the Administration-level Privacy Officers. The Undersecretaries of Health, Benefits and Memorial Affairs designate Administration Privacy Officers to lead their Administration’s Privacy Program. They develop Administration policy and implementation guidance that assigns responsibilities and duties to all Privacy Officers within their respective areas.
The responsibilities of Administration Privacy Officers include:
- Developing and implementing Administration-wide privacy policies and procedures.
- Providing input to the VA Privacy Service Director to develop privacy policies and initiatives. After implementing these policies, provide feedback on their effectiveness.
- Implementing the VA Privacy Program within their respective areas.
- Understanding and applying Federal law, regulations, and VA Directives related to privacy.
- Serving as advisors on all aspects of privacy in their Administration.
- Creating and promoting a proactive privacy environment within their Administration.
- Determining the need for field-based Privacy Officers within their Administrations.
- Providing instruction regarding responsibilities and requirements to implement the VA Privacy program within field-based facilities.
3.5 VA Privacy Officers
VA requires the head of every VA Staff Office and Facility to designate a Privacy Officer. The Privacy Officer is responsible for establishing and maintaining a sustainable local Privacy Program that complies with VA and Administration-level privacy policies and procedures. The Privacy Officer effectively manages privacy risks in the information systems and operations within their realm of responsibilities.
The responsibilities of VA Privacy Officers are:
- Establishing and implementing privacy policies.
- Understanding and applying federal law, regulations, guidance, and VA policy related to privacy.
- Serving as advisor and primary contact for privacy.
- Administering privacy training and awareness programs within their realm of responsibility.
- Working with the appropriate parties to identify, publish, and update SORNS in accordance with VA Handbook 6300.5, Procedures for Establishing and Maintaining Privacy Act Systems of Records.
- Collaborating with local Record Officers or Records Liaison Officers to implement processes for proper retention and disposal of records that contain PII.
- Providing notice through Privacy Act statements when the VA collects information from members of the public.
- Creating and promoting a proactive privacy environment within their organizations.
- Responding appropriately to all privacy complaints under their purview of responsibility.
- Reporting all actual or suspected privacy incidents into the designated data breach reporting system within one hour of discovery or notification.
- Completing all assigned PTAs and PIAs in accordance with VA Directive 6508, Implementation of Privacy Threshold Analysis and Privacy Impact Assessment.
- Including privacy language in contracts to properly safeguard PII in accordance with VA 6500.6, Contract Security.
- Providing support to Information System Owners (ISO), Information System Security Officer (ISSO) and VA Privacy Service to address privacy-related controls in accordance with VA Handbook 6500, Risk Management Framework for VA Information Systems VA Information Security Program and other VA-issued control guidance and policies.
4. Fair Information Practice Principles
The VA Privacy Program adheres to the Fair Information Practice Principles (FIPPs). VA uses the FIPPs when evaluating information systems, processes, programs, and activities that affect individual privacy. The FIPPs include:
Openness. When VA collects personal data from an individual, VA will inform him or her of the intended uses of the data, the disclosures that will be made, the authorities for the data’s collection and whether the collection is mandatory or voluntary. No VA office will collect data subject to the Privacy Act unless a Privacy Act system notice has been published in the Federal Register and posted on the VA System of Records Notices Website, available at: Privacy Act System of Records Notices (SORNs) – Privacy.
Individual Participation. Unless VA has claimed an exemption from the Privacy Act, everyone will be granted access to his or her records, upon request; to the extent permitted by law and provided a list of disclosures made outside VA; and provided the opportunity to make corrections to his or her file if it is shown to be in error.
Limited Collection. VA will collect only those personal data elements required to fulfill an official function or mission grounded in law. Those collections will be conducted by lawful and fair means.
Limited Retention. VA will retain personal information only for as long as necessary to fulfill the purposes for which it is collected. Records will be destroyed in accordance with established VA records management principles.
Data Quality. VA will make every effort to maintain only accurate, relevant, timely and complete data about individuals.
Limited Internal Use. VA will use personal data for lawful purposes only. Access to any personal data will be limited to those individuals within VA with an official need for the data.
Disclosure. VA personnel will zealously guard all personal data to ensure that all disclosures are made with written permission or in strict accordance with privacy statutes.
Security. All personal data will be protected by safeguards appropriate to ensure security and confidentiality. Electronic systems will be periodically reviewed for compliance with the security principles of the Privacy Act, the Computer Security Act, HIPAA, and related statutes. Electronic collection of information will only be conducted in a safe and secure manner.
Accountability. VA, its employees, and contractors are subject to civil and criminal penalties for certain breaches of privacy. VA officials will be diligent in sanctioning individuals who violate privacy rules.
Challenging Compliance. An individual may challenge VA if he or she believes that VA has failed to comply with these principles, privacy statutes, or the rules in a SORN.
5. Privacy Risk Management
VA establishes and uses a multi-level risk management approach that addresses security and privacy risk at the organizational level, the mission/business process level, and the information system level. This is consistent with National Institute of Standards and Technology (NIST) SP 800-139, Managing Information Security Risk: Organization, Mission, and Information System View.
5.1 Implementation of the VA Risk Management Framework
VA follows the principles established in NIST 800-37, Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy. This incorporates security and privacy risk management activities into the system development lifecycle. The SAOP works in coordination with the VA Chief Information Security Officer to:
- Review and approve the categorization of information systems that create, collect, use, process, store, maintain, disseminate, disclose, or dispose of PII in accordance with Federal Information Processing Standard (FIPS) Publication 199, Standards for Security Categorization of Federal Information and Information Systems, and NIST SP 800-60, Guide for Mapping Types of Information and Systems to Security Categories.
- Review authorization packages for information systems that create, collect, use, process, store, maintain, disseminate, disclose, or dispose of PII, to manage privacy risks prior to system authorization.
- Determine whether additional measures are required to manage privacy risks prior to authorization.
VA maintains an Information Security Knowledge Service which provides enterprise RMF policy and implementation guidance. The Knowledge Service also includes a Security Controls Explorer (SCE) that addresses NIST SP 800-53 security and privacy requirements. The SCE also provides control implementation policy and compliance criteria related to VA’s RMF and integration of security and privacy controls.
5.2 Privacy Control Requirements
VA implements NIST SP 800-53 privacy requirements. The SAOP designates which privacy controls VA will treat as program management, common, system-specific, or hybrid controls. Privacy Program management controls are controls that are generally implemented at the agency level and essential for managing the agency’s privacy program. Multiple information systems inherit common controls. Information system-specific controls are controls that are implemented for a particular information system or the portion of a hybrid control that is implemented for a particular information system. Hybrid controls are controls that are implemented for an information system in part as a common control and in part as an information system-specific control. The determination as to whether a privacy control is a common, hybrid, or information system-specific control is based on context. See Appendix B: Privacy Control Allocation
5.3 Privacy Overlays
The VA Privacy Program leverages privacy overlays established by the Committee on National Security Systems Instruction (CNSSI) No. 1253, Appendix F – Attachment 6 for national security systems as guidance when selecting and assessing effectiveness of privacy protections. An overlay specifies security controls, control enhancements, supplemental guidance, and other supporting information. The purposes of the privacy overlays include providing standard security and privacy control baselines for systems containing PII. Privacy considerations are integrated into the system development life cycle and security processes in the early stages and guide privacy requirements for PHI.
5.4 Privacy Continuous Monitoring (PCM)
The SAOP establishes and maintains a VA-wide PCM Program that implements VA’s PCM Strategy. The design of the PCM Program is to maintain ongoing awareness of threats and vulnerabilities that may pose privacy risks, monitor changes to information systems that process PII. VA conducts privacy control assessments to verify the continued effectiveness of all privacy controls to comply with privacy requirements and manage privacy risks.
VA PCM efforts assess programmatic and information system privacy controls across VA Administrations and Staff Offices.

VA Privacy Assessments that Monitor VA Privacy Controls
6. Requirements for Handling Personally Identifiable Information
6.1 Recognizing PII
Personally Identifiable Information (PII) is a type of Controlled Unclassified Information (CUI), which includes SPI, PHI, and Federal Tax Information (FTI). Examples of PII are Veteran medical records, personal and financial employee records, and credit card information.
PII refers to an individual’s information that distinguishes or traces an individual’s identity, alone, or when combined with other identifying information. These include name, Social Security Number (SSN), biometric records, date and place of birth, mother’s maiden name, medical information, personal financial information, credit card account numbers, passport numbers, criminal history or information that may stigmatize or adversely affect an individual. The term SPI is used interchangeably with PII.
- PHI, as defined by the Health Insurance Portability and Accountability Act (HIPAA) Privacy Rule, is individually identifiable health information transmitted or maintained in any form or medium by a covered entity, such as VHA. This is another subcategory of PII. Note: VHA uses the term PHI to define information covered by HIPAA but, unlike individually identifiable health information, may or may not be covered by the Privacy Act of 1974 or Title 38 VA Confidentiality Statutes as updated. In addition, PHI excludes employment records held by VHA in its role as an employer.
- FTI includes tax returns or information about those returns that can come directly from the Internal Revenue Service (IRS) or other secondary sources like other federal agencies.
6.2 Minimizing the Collection PII
The Privacy Act of 1974 requires that federal agencies collect only relevant and necessary information about individuals. OMB A-130, Managing Information as a Strategic Resource, directs federal agencies to limit the creation, collection, use, processing, storage, maintenance, dissemination, and disclosure of PII to that which is legally authorized, relevant, and reasonably deemed necessary to properly perform agency functions.
VA maintains an inventory of PII holdings and uses the PTA, PIA and SORN review and approval process to identify reduction opportunities and to ensure, to the maximum extent practicable, that such holding is accurate, relevant, timely, and complete. In addition, the VA has established process requirements for justifying the collection, maintenance, and uses of Social Security Numbers (SSNs) as directed in VA Directive 6507, Reducing the Use of Social Security Numbers.
6.3 Handling and Transmitting PII
PII requires strict handling guidelines due to the nature of the information and the increased risk to an individual for compromised information. VA guidance for the handling of PII by VA staff includes:
- Always store paper documents containing VA sensitive information securely when not in use.
- Make sure to clear your work area and secure any documents containing VA sensitive information before screensharing, turning on video, or leaving the room.
- When mailing sensitive documents, make sure that the envelopes are addressed correctly and contain only content intended for that recipient.
- Before faxing sensitive documents, confirm that the connection is secure, verify the fax number, and ensure that an authorized person is on the receiving end.
- Store electronic files and documents containing VA sensitive information on properly secured shared drives.
- Access only to information, programs, and systems that you need to perform your official duties and never provide access to information to anyone who doesn’t have an authorized need-to-know.
- Encrypt sensitive PII on computers, email, media, and other devices.
- Report suspected or identified privacy and security incidents to their supervisor, Information System Security Officer, and Privacy Officer immediately.
7. Privacy Compliance Process
VA Privacy Program works in partnership with program, technical, development, legal, security and privacy teams across VA to assess the privacy risk of VA Information Technology (IT) systems, technologies, pilot projects, rulemakings, web-based developed systems, information collections, programs, and/or projects (collectively referred to as “information systems”). The team works collaboratively to develop mitigation strategies by reviewing and approving all VA privacy compliance documentation.
VA’s privacy compliance process is an ongoing cycle with four key parts to ensure appropriate oversight: PTA, PIA, SORN and Periodic Review. Each part functions in implementing privacy policy at VA, and together enhance the oversight of and transparency into activities and demonstrate accountability to the public.
7.1 Privacy Threshold Analysis
A PTA is an initial privacy assessment used to determine if the information system contains PII and whether a PIA or a SORN is required, and if any other privacy requirements apply to the information system.
VA uses the PTA to:
- Identify IT systems, programs and projects that have privacy implications.
- Demonstrate the inclusion of privacy considerations during the review of an IT system, program, project, or boundary.
- Provide a record of the program, system, or boundary and its privacy requirements.
- Demonstrate compliance with privacy laws and regulations.
VA requires all VA information system to complete a PTA to obtain an ATO as a part of VA’s A&A process.
7.2 Privacy Impact Assessment
Section 208 of the E-Government Act of 2002 requires all federal agencies to conduct a PIA for all new or substantially changed technology that collects, maintains, or disseminates PII. A PIA is an analysis of how information is handled to ensure handling conforms to applicable legal, regulatory, and policy requirements regarding privacy.
VA uses the PIA to:
- Determine the risks and effects of collecting, maintaining, and disseminating PII in a system.
- Examine and evaluate protections and alternative processes for handling information to mitigate potential privacy risks.
- demonstrates that program managers and system owners have consciously incorporated privacy protections throughout the development life cycle of a system or program.
- provide the public with information about the VA’s collection and use of PII.
VA requires all privacy sensitive information system owners, as determined by the PTA, to complete a PIA to obtain an ATO as a part of VA’s A&A process.
A listing of VA PIAs is available at: Privacy Impact Assessments (PIA)
7.3 System of Records Notice
VA follows OMB Circular A-108, Federal Agency Responsibilities for Review, Reporting, and Publication under the Privacy Act to meet the requirements for implementing the review, reporting, and publication requirements of the Privacy Act of 1974 and related OMB policies.
The Privacy Act requires agencies to publish a SORN in the Federal Register describing the existence and character of a new or significantly modified systems of records (SOR). SORs include any group of records created and maintained by the agency about individuals, which retrieves information by a name or another unique identifier.
A SORN informs the public about what kinds of personal information federal agencies maintain; limits the uses and disclosures of the information to those compatible with the law permitting its collection; and describes how an individual might request access to their information or to seek redress otherwise.
A list of VA published SORNs and related policies is available at: Privacy Act System of Records Notices (SORNs) – Privacy
7.3.1 SORN Reviews and Update
VA publishes a SORN in the Federal Register under the following circumstances:
- When establishing a new SORs.
- When making significant changes to an existing SORs. A significant change is substantive in nature and warrants a revision of the SORN to provide notice to the public of the character of the modified SOR. The following are examples of a significant change:
- Expanding the category of records
- Change in the authority for maintenance.
- New/modified routine use.
- Promulgation of a rule to exempt a SORs.
VA Privacy Program provides oversight and guidance to the SORN System Managers throughout the development and modification of SORNs. SORN System Managers work with the appropriate parties to publish SORNs for all systems of records. They ensure that procedures for access, correction, or amendment of records conform to VA requirements documented in VA Handbook 6300.5 Procedures for Establishing and Maintaining Privacy Act Systems of Records and follow VA regulations governing Privacy.
7.3.2 Reporting SORNS to OMB and Congress
VA reports all new/modified changes for a SORN to OMB and Congress following the prescribed requirements identified in OMB Circular A-108 Federal Agency Responsibilities for Review, Reporting, and Publication under the Privacy Act. The Privacy Act of 1974 requires each federal department that proposes to establish or significantly modify a SOR to provide adequate advance notice of any such proposal to:
- Office of Management and Budget
- Committee on Oversight and Accountability of the U.S. House of Representatives
- Committee on Homeland Security and Governmental Affairs of the U.S. Senate
VA currently reports the following to Congress:
- A transmittal letter signed by the SAOP.
- A narrative statement (this includes a brief overview of the SORs, including an evaluation of the probable or potential effect on the privacy of individuals).
- A draft Federal Register notice.
- Any Privacy Act exemption rules.
- Supplementary documents (as needed).
7.3.3 Privacy Act Statements
When requesting individuals’ information that will become part of a SOR, VA provides a Privacy Act Statement on the form used to collect the information or on a separate form that the individual can retain. VA provides the Privacy Act Statement in compliance with the Paperwork Reduction Act (PRA). This is regardless of whether paper or electronic form, on a website, on a mobile application, over the telephone, or through some other medium collects the information. This provides sufficient information to the individual to make an informed decision on whether to respond.
The Privacy Act Statement outlines relevant information from the SORN such as:
- The authority (whether granted by statute, or by Executive Order of the President) which authorizes soliciting the information and whether disclosure of such information is mandatory or voluntary.
- The principal purpose or purposes for the use of the information.
- The published routine uses to which the information is subject.
- The effects on the individual, if any, of not providing all or any part of the requested information.
- Any appropriate citation (and if practicable, a link) to the relevant SORNs.
8. Computer Matching Programs
The Privacy Act, the Computer Matching and Privacy Protection Act of 1988, and the Payment Integrity Information Act (PIIA) require oversight and approval for VA computer matching activities. CMAs are between VA and partner agencies or non-federal agencies that allow parties to engage in CMPs. A CMP is a computerized comparison of records. The purpose is to establish or verify eligibility or recoup payments for a federal benefit program or relating to federal personnel management. The VA Data Integrity Board (DIB) oversees and approves all VA CMP activities. Members of the DIB include the SAOP, VA Privacy Service Director, VHA, VHA, VBA, Office of the Inspector General, and the Office of Management. VA publishes CMAs in the Federal Register when VA is the recipient agency for a re-establishment matching program.
The list of published CMAs is available at: Computer Matching Agreements (CMA) – Privacy.
8.1 Computer Matching Act – Annual Reporting
The Computer Matching Act requires VA to implement annual reporting requirements. Under VA Handbook 6502.4, Procedures for Matching Agreements, VA compiles and submits annual reports to Congress and OMB detailing the following:
- Current information about the composition of the DIB.
- A list of each matching program in which VA participated during the year.
- For each matching program for which the DIB waived the requirement for a cost-benefit analysis and the reasons for the waiver.
- A description of any matching agreement that the DIB disapproved of and the reasons for the disapproval.
- A description of any alleged or identified violations of matching agreements and a discussion of any action taken in response.
The DIB’s annual matching activity report may also include a review of any VA matching activities that are not matching programs.
Congress and OMB require VA to provide an advanced notice when a matching program is new, re-established, or significantly modifies a current matching program.
The Computer Matching Activities Report for the current calendar year is available at: Publicly Available Agency Reports on Privacy.
9. Enterprise Social Security Number Reduction Program
VA is taking steps to reduce and, where possible, eliminate the use of the SSNs for uniquely identifying individuals in VA operations, programs, and information systems. VA Enterprise Social Security Number Reduction (ESSNR) is an ongoing program initiated by the Office of Management and Budget Memorandum 07-16, Safeguarding Against and Responding to the Breach of Personally Identifiable Information. Other Federal legislation drives the ESSNR, such as the Social Security Number Fraud Prevention Act of 2017 and the Consolidated Appropriations Act, 2024, P.L. 118-42, Division A, Title II (Sec. 237).
The Social Security Number Fraud Prevention Act of 2017 prohibits the inclusion of SSNs on any document sent by mail. The head of the agency can determine that the SSN inclusion is necessary per the authority of 38 U.S.C. 5101 Final Rule (RIN-2900-AR19). Federal Register: Social Security Number Fraud Prevention Act of 2017 Implementation.
As required by the Fraud Prevention Act of 2017, VA removed SSNs from Veteran Identification Cards, prescription labels, mailing labels, several forms, and most appointment letters. The SSN is mailed and pre-populated with full SSN for the documents listed on the web page: Social Security Number Reduction (SSNR).
The Consolidated Appropriations Act, 2024, Public Law 118-42 (Division A, Title II, Sec. 237) requires VA to discontinue collecting and using SSNs to authenticate individuals in all VA information systems no later than September 30, 2024. VA may continue to collect and use SSN to identify an individual in accordance with the Privacy Act in an information system if it is necessary to 1) obtain or provide required information from a system that is not under the jurisdiction of the Secretary; 2) comply with a law, regulation, or court order; 3) perform anti-fraud activities; or 4) identify a specific individual where no adequate substitute is available. VA will comply with this legislation through a multi-year phased approach that includes system modifications, user and Veteran re-education and awareness campaigns.
10. Budget and Acquisition
The CPO reviews IT capital investment plans and budgetary requests to ensure that privacy requirements and associated privacy controls, as well as any associated costs, are explicitly identified and included. This is with respect to any IT resources used to create, collect, use, process, store, maintain, disseminate, disclose, or dispose of PII. The CPO serves as an advisor for privacy on the Program and Acquisition Review Council (PARC).
The PARC supports the OIT in meeting the needs of its business owners through managing, overseeing, and executing the VA IT budget. The PARC also manages the formation and executes core VA portfolios, such as VHA, VBA, NCA, and VA Corporate. The PARC provides a forum for deliberation, and when necessary, escalation to the OIT Governance Board (ITGB) regarding VA’s IT investments needed to achieve VA and OIT mission and business requirements.
11. Contractors and Third Parties
VA ensures that contractors, subcontractors, and third-party servicers or associates, and those working on behalf of any of these entities, employ adequate security and privacy controls in accordance with VA directives and handbooks, regulations, guidance, and established service level agreements. The VA Privacy Program coordinates with the Office of Acquisitions, Logistics and Construction to include the applicable privacy clauses in the terms and conditions of contracts and other agreements as outlined in VA Handbook 6500.6, Contract Security.
VA requires Program Managers, Contracting Officer Representatives, Privacy Officers and Information System Security Officers to complete VA Handbook 6500.6 Contract Security Appendix A Checklist for Information Security in the Initiation Phase of Acquisition at the initiation of IT service acquisitions, statements of work (SOWs), third-party service agreements, and any other legally binding agreement. The checklist determines what, if any, privacy controls are necessary. This ensures the services, systems, and/or products being procured comply with existing privacy laws and policies regarding the protection, maintenance, dissemination, and disclosure of information.
12. Privacy Workforce Management
The SAOP assesses and addresses the hiring, training, and professional development needs of the Department with respect to privacy. Additionally, the SAOP who also serves as the VA Chief Information Officer, coordinates with the Chief Human Capital Officer (or Office of Human and Administration) and OIT Chief People Officer to establish and maintain VA’s workforce planning process; assess workforce skills; recruit and retain privacy and IT professionals; develop competency requirements for IT and privacy staff; and ensure managers are aware of flexible hiring authorities.
The SAOP issues Department-wide privacy workforce management policies such as VA Directive 6509, Duties of Privacy Officers, which require VA Executives (e.g., Under Secretaries, Assistant Secretaries, and Other Key Officials) to designate Privacy Officers at the Administration, Staff Office, and Facility levels; review skill sets and effectiveness of all Privacy Officers; assess the adequacy of current privacy staffing levels at all VA facilities; provide the resources necessary to designate Privacy Officers; and periodically reassess the necessity of additional Privacy Officers.
The SAOP, in collaboration with the VA CPO and OIT Chief People Officer, facilitates and oversees Department-wide and role-based privacy training for VA’s workforce. This is to ensure VA personnel have the appropriate knowledge and skills to embed privacy into their respective business processes.
This includes:
- VA Privacy Officer Professionalization Training Program provides Privacy Officers with resources necessary to support their professional development and privacy education. This includes the VA Privacy Hub which serves as a one-stop shop for VA Privacy Officers and privacy professionals to quickly and easily access resources to execute their duties; Privacy Webinars and Training on critical and emerging privacy topics; and Technical Documents and Job Aids providing instructions on how to complete daily critical tasks and perform privacy assessments of systems and programs.
- VA Cyber Workforce Program designed to develop programs for VA to leverage to improve recruitment, retention, development, and growth opportunities for cyber professionals, as defined by the National Initiative for Cybersecurity Education (NICE) Framework. This includes the Career Development Portal, which offers a diverse set of skills-based learning opportunities based on the NICE Work Roles (e.g., Privacy Compliance Manager) in the fields of IT, cybersecurity, cross-functional, and artificial intelligence areas.
13. Privacy Awareness and Training Program
VA Privacy Awareness and Training Program equips VA’s workforce with the knowledge and future skills necessary to handle personal information responsibly, respond appropriately and effectively to privacy risks, and comply with information protection laws and regulations. VA Privacy Awareness and Training Programs provide guidance that includes privacy awareness, general and privacy role-based training for employees, contractors, volunteers, and business associates.
13.1 Privacy Awareness Training and Rules of Behavior Training
VA Directive 6502, Enterprise Privacy Program, requires all employees, contractors, volunteers, and business associates to complete initial (first 90 days) and annual mandatory VA Privacy and Information Security Awareness and Rules of Behavior training course and sign VA Information Security Rules of Behavior. VA reviews and updates this mandatory training and rules of behavior on an annual and ad-hoc basis to ensure it is consistent with federal and VA policies, standards and guidelines and address new and emerging privacy risks impacting VA and Veterans.
13.2 Privacy Role-based Training
VA requires employees and contractors who have significant privacy responsibilities (based upon position and/or laws that apply to information being access) to complete additional advanced mandatory privacy role-based training courses.
These training courses include:
- Privacy and HIPAA – provides guidance on privacy practices for the use and disclosure of PHI and Veteran rights regarding VHA information. This course is an annual mandatory requirement for employees and contractors with access to PHI and/or VHA computer system in accordance with VHA Directive 1605.1, Privacy and Release of Information.
- Information Security and Privacy Role-Based (ISP) Training Courses – provide the requirements, policies, standards, and additional resources concerning information security and privacy controls, consistent with the Federal Information Security Modernization Act (FISMA), National Institute of Standards and Technology (NIST) guidance, and VA Directive and Handbook 6500, Risk Management Framework for VA Information Systems VA Information Security Program.
- Mandatory ISP course for the following roles: Software Developers; Law Enforcement Professionals Information System Owners; Acquisition Personnel; and Leaders.
13.3 Privacy Awareness and Outreach
VA conducts awareness and outreach campaigns and activities to communicate privacy and security resources, products, and techniques to VA employees and contractors. This supports VAs ongoing efforts to the number of privacy incidents; shifting behaviors, attitudes, and perspectives of internal stakeholders regarding privacy; and establishing privacy as a priority throughout VA. Outreach campaigns include:
- Monthly newsletter to Privacy Officers.
- News and information to employees across VA through blog posts, social media, videos, and posters and fliers.
- Multiple webinars yearly through the VA Privacy in Action Speaker Series.
- Participating and developing resources for Data Privacy Week, Information Security and Privacy Awareness Week (ISPAW), and National Cybersecurity Awareness Month (NCSAM).
14. Data Breach Response
The Data Breach Response Service (DBRS) has the sole responsibility of data breach oversight and management within the VA. DBRS is the lead organization for adjudicating and handling Privacy/Security related incidents. The Privacy and Security Events Tracking System (PSETS) is the official SOR to record/track/close all complaints and incidents that occur at the VA.
The DBRS reviews each event in PSETS to validate whether it is either a complaint or an incident. DBRS reviews all incidents in accordance with federal requirements and VA policies and directives to assess the risk of exposure to identity theft. DBRS refers complex breaches to the Data Breach Core Team (DBCT) for incident handling and includes it in the OIT daily brief to the CIO. DBRS refers cybersecurity events/incidents to the Cybersecurity Operations Center (CSOC) since they may also be Privacy or Data Breaches as outlined in VA Handbook 6500.2, Management of Breaches Involving Sensitive Personal Information. The Director of DBRS escalates incidents in accordance with HIPAA and other applicable regulations and reporting requirements.
14.1 Data Breach Core Team
The Director of DBRS chairs the DBCT. Membership consists of the entire DBRS staff, CPO, representatives of the Office of General Counsel (OGC), VHA Privacy Service, OIT Privacy Service, Field Security Service, Office of Congressional and Legislative Affairs, Office of Public and Intergovernmental Affairs, Board of Veterans Appeals (BVA), VHA, VBA, NCA, Human Resources Information Service, and Office of Acquisition and Logistics.
The DBCT adjudicates specific incidents to determine the type of event, impact, and reporting requirements. DBCT works with the DBRS in analyzing, addressing, and mitigating breaches to ensure timeliness, uniformity, and visibility of VA responses. DBCT assists the DBRS in determining the need for notification and credit protection offers involving 50 or more individuals if their PII/PHI/SPI is part of a breach.
14.2 Privacy and Security Events Tracking System
Local ISSOs and POs enter all reported complaints, and incidents into the PSETS database within one (1) hour of identifying or receiving notification of an incident or complaint. The VA breach management process begins with local ISSOs and POs gathering information, determining whether an incident has occurred and completing the local risk assessment as necessary. After completing these steps, the facility level incident response team, in collaboration with the DBRS, conducts further analysis as necessary. They manage incident responses for breaches. The DBRS reviews the entries in the PSETS database daily, evaluates them for clarity and internal consistency, and determines required action. Further action may include notification, credit protection, or referral to the DBCT for additional analysis.
14.3 Congressional Quarterly Reports on VA Data Breaches
In accordance with the Veterans Benefits, Health Care, and Information Technology Act of 2006 (P.L. 109-461), VA must submit a report on any data breach with respect to the SPI processed or maintained by the Department during a given quarter. VA submits the reports to the Committees on Veterans’ Affairs of the Senate and House of Representatives. Each report submitted includes:
- Date of Incident and Location of Event.
- Number of Notification Letters and Credit Protection Letters pending or sent.
- The status of remedial or corrective action with respect to the breach.
Quarterly Report to Congress on Data Incidents reports for the current fiscal year is available at: Publicly Available Agency Reports on Privacy – Privacy. VA Privacy Program Website and Digital Services
VA’s Privacy Program public facing website at https://www.va.gov/privacy contains information on VA privacy practices such as privacy compliance; safeguarding information; privacy training resources; privacy laws, policies, and guidance; and contact information. Any privacy questions, concerns, or complaints are addressed by contacting VA Privacy Service at (202) 273-5070 or privacyservice@va.gov.
The VA applies leading privacy practices and adheres to data stewardship principles in managing web user information. The data stewardship principles guiding our efforts include the following goals:
- Protecting web user privacy
- Maintaining the confidentiality of web user information
- Ensuring appropriate levels of security for web user data
VA Web Privacy Policies describe how VA applies these principles to the handling of personal information provided to VA websites and forms. Personal information may include name; email, home, and/or business address; phone numbers; SSN; or other personal identifying information.
15. VA Privacy Policies
VA issues mandatory enterprise privacy policies (referred to as “Directives”) and accompanying mandatory enterprise privacy procedures or operational requirements for implementing the policy requirements in the directive (referred to as “Handbooks”). VA Privacy Directives and Handbooks provide guidance to include the specific roles and responsibilities of VA staff in ensuring compliance with federal privacy laws, regulations and policy and managing the privacy risks to individuals. All publicly available VA Privacy Directives and Handbooks are available at: VA Privacy Policies
Appendix A: Acronyms
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Acronym | Definition |
|---|---|---|---|---|---|---|
| 1 | A&A | Assessment and Authorization | ||||
| 2 | AP | Authority and Purpose | ||||
| 3 | AR | Accountability, Audit, and Risk Management | ||||
| 4 | ASIT | Assistant Secretary for Information and Technology | ||||
| 5 | ATO | Authorization to Operate | ||||
| 6 | BVA | Board of Veterans Appeals | ||||
| 7 | CIO | Chief Information Officer | ||||
| 8 | CMA | Computer Matching Agreement | ||||
| 9 | CMP | Computer Matching Program | ||||
| 10 | CNSSI | Committee on National Security Systems Instruction | ||||
| 11 | CPO | Chief Privacy Officer | ||||
| 12 | CSOC | Cybersecurity Operations Center | ||||
| 13 | CUI | Controlled Unclassified Information | ||||
| 14 | DBCT | Data Breach Core Team | ||||
| 15 | DBRS | Data Breach Response Service | ||||
| 16 | DI | Data Quality and Integrity | ||||
| 17 | DIB | Data Integrity Board | ||||
| 18 | DM | Data Minimization and Retention | ||||
| 19 | ERM | Enterprise Risk Management | ||||
| 20 | ESSNR | Enterprise Social Security Number Reduction Program | ||||
| 21 | FIPPs | Fair Information Practice Principles | ||||
| 22 | FIPS | Federal Information Processing Standards | ||||
| 23 | FISMA | Federal Information Security Modernization Act of 2014 | ||||
| 24 | FTI | Federal Tax Information | ||||
| 25 | HIPAA | Health Insurance Portability and Accountability Act | ||||
| 26 | IP | Individual Participation and Redress | ||||
| 27 | IRS | Internal Revenue Service | ||||
| 28 | ISO | Information System Owner | ||||
| 29 | ISP | Information Security and Privacy | ||||
| 30 | ISPAW | Information Security and Privacy Awareness Week | ||||
| 31 | ISSO | Information System Security Officer | ||||
| 32 | IT | Information Technology | ||||
| 33 | ITGB | OIT Governance Board | ||||
| 34 | MOU/ISA | Memorandum of Understanding/Interconnection Security Agreement | ||||
| 35 | NARA | National Archives and Records Administration | ||||
| 36 | NCA | National Cemetery Administration | ||||
| 37 | NCSAM | National Cybersecurity Awareness Month | ||||
| 38 | NICE | National Initiative for Cybersecurity Education | ||||
| 39 | NIST | National Institute of Standards and Technology | ||||
| 40 | OGC | Office of General Counsel | ||||
| 41 | OIT | Office of Information and Technology | ||||
| 42 | OMB | Office of Management and Budget | ||||
| 43 | PARC | Program and Acquisition Review Council | ||||
| 44 | PCM | Privacy Continuous Monitoring | ||||
| 45 | PHI | Protected Health Information | ||||
| 46 | PIA | Privacy Impact Assessment | ||||
| 47 | PII | Personally Identifiable Information | ||||
| 48 | PIIA | Payment Integrity Information Act | ||||
| 49 | PO | Privacy Officer | ||||
| 50 | PPP | Privacy Program Plan | ||||
| 51 | PRA | Paperwork Reduction Act | ||||
| 52 | PSETS | Privacy and Security Events Tracking System | ||||
| 53 | PTA | Privacy Threshold Analysis | ||||
| 54 | PTR | Privacy Training | ||||
| 55 | RMF | Risk Management Framework | ||||
| 56 | SAOP | Senior Agency Official for Privacy | ||||
| 57 | SE | Security | ||||
| 58 | SOR | System of Records | ||||
| 59 | SORN | System of Records Notice | ||||
| 60 | SOW | Statements of Work | ||||
| 61 | SP | Special Publication (i.e., NIST SP) | ||||
| 62 | SPI | Sensitive Personal Information | ||||
| 63 | SPP | System Privacy Plan | ||||
| 64 | SSN | Social Security Number | ||||
| 65 | SSNR | Social Security Number Reduction | ||||
| 66 | TR | Transparency | ||||
| 67 | UL | Use Limitation | ||||
| 68 | VA | Department of Veterans Affairs | ||||
| 69 | VBA | Veterans Benefits Administration | ||||
| 70 | VHA | Veterans Health Administration |
Appendix B: Privacy Control Allocation
Control Types Designations
- Common: Single implementation leveraged and used uniformly across VA.
- Hybrid: Implementation is split between two or more elements of VA.
- System-Specific: Implementation is unique to the specific information system.
VA designates program management controls as common/inheritable in its Governance, Risk, and Compliance tool (Enterprise Mission Assurance Support Service, or eMASS) to align with the Department of Defense. VA is currently transitioning to NIST SP 800-53 Rev 5 controls and will update this project plan when implemented.
Family: Authority and Purpose (AP)
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | ID | Privacy Controls | Designation |
|---|---|---|---|---|---|---|---|
| 1 | AP-1 | Authority to Collect | System-Specific | ||||
| 2 | AP-2 | Purpose Specification | System-Specific |
Family: Accountability, Audit, and Risk Management (AR)
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | ID | Privacy Controls | Designation |
|---|---|---|---|---|---|---|---|
| 2 | AR-1 | Governance and Privacy Program | Common | ||||
| 3 | AR-2 | Privacy Impact and Risk Assessment | Hybrid | ||||
| 4 | AR-3 | Privacy Requirements for Contractors and Service Providers | Hybrid | ||||
| 5 | AR-4 | Privacy Monitoring and Auditing | Hybrid | ||||
| 6 | AR-5 | Privacy Awareness and Training | Hybrid | ||||
| 7 | AR-6 | Privacy Reporting | Common | ||||
| 8 | AR-7 | Privacy-Enhanced System Design and Development | System-Specific | ||||
| 9 | AR-8 | Accounting of Disclosures | System-Specific |
Family: Data Quality and Integrity (DI)
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | ID | Privacy Controls | Designation |
|---|---|---|---|---|---|---|---|
| 1 | DI-1 | Data Quality | Hybrid | ||||
| 2 | DI-1(1) | Data Quality | Validate PII | System-Specific | ||||
| 3 | DI-1(2) | Data Quality | Re-Validate PII | Hybrid | ||||
| 4 | DI-2 | Data Integrity and Data Integrity Board | Common | ||||
| 5 | DI-2(1) | Data Integrity and Data Integrity Board | Publish Agreements on Website | System-Specific |
Family: Data Minimization and Retention (DM)
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | ID | Privacy Control | Designation |
|---|---|---|---|---|---|---|---|
| 1 | DM-1 | Minimization of Personally Identifiable Information | Hybrid | ||||
| 2 | DM-1 (1) | Minimization of Personally Identifiable Information | Locate/Remove/Redact/Anonymize PII | Hybrid | ||||
| 3 | DM-2 | Data Retention and Disposal | Hybrid | ||||
| 4 | DM-2(1) | Data Retention and Disposal | System Configuration | Hybrid | ||||
| 5 | DM-3 | Minimization of PII Used in Testing, Training, and Research | Hybrid | ||||
| 7 | DM-3(1) | Minimization of PII Used in Testing, Training, and Research | Risk Minimization Techniques | Hybrid |
Family: Individual Participation and Redress (IP)
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | ID | Privacy Controls | Designation |
|---|---|---|---|---|---|---|---|
| 1 | IP-1 | Consent | System-Specific | ||||
| 2 | IP-1(1) | Consent | Mechanisms Supporting Itemized or Tiered Consent | Hybrid | ||||
| 3 | IP-2 | Individual Access | Hybrid | ||||
| 4 | IP-3 | Redress | Hybrid | ||||
| 5 | IP-4 | Complaint Management | Hybrid | ||||
| 6 | IP-4(1) | Complaint Management | Response Times | Hybrid |
Family: Security (SE)
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | ID | Privacy Controls | Designation |
|---|---|---|---|---|---|---|---|
| 1 | SE-1 | Inventory of Personally Identifiable Information | Hybrid | ||||
| 2 | SE-2 | Privacy Incident Response | Hybrid |
Family: Transparency (TR)
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | ID | Privacy Controls | Designation |
|---|---|---|---|---|---|---|---|
| 1 | TR-1 | Privacy Notice | Hybrid | ||||
| 2 | TR-1(1) | Privacy Notice | Real-Time or Layered Notice | System-Specific | ||||
| 3 | TR-2 | System of Records Notices and Privacy Act Statements | Hybrid | ||||
| 4 | TR-2(1) | System of Records Notices and Privacy Act Statements | Public Website Publication | Common | ||||
| 5 | TR-3 | Dissemination of Privacy Program Information | Common |
Family: Use Limitation (UL)
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | ID | Privacy Controls | Designation |
|---|---|---|---|---|---|---|---|
| 25 | UL-1 | Internal Use | System-Specific | ||||
| 26 | UL-2 | Information Sharing with Third Parties | System-Specific |

